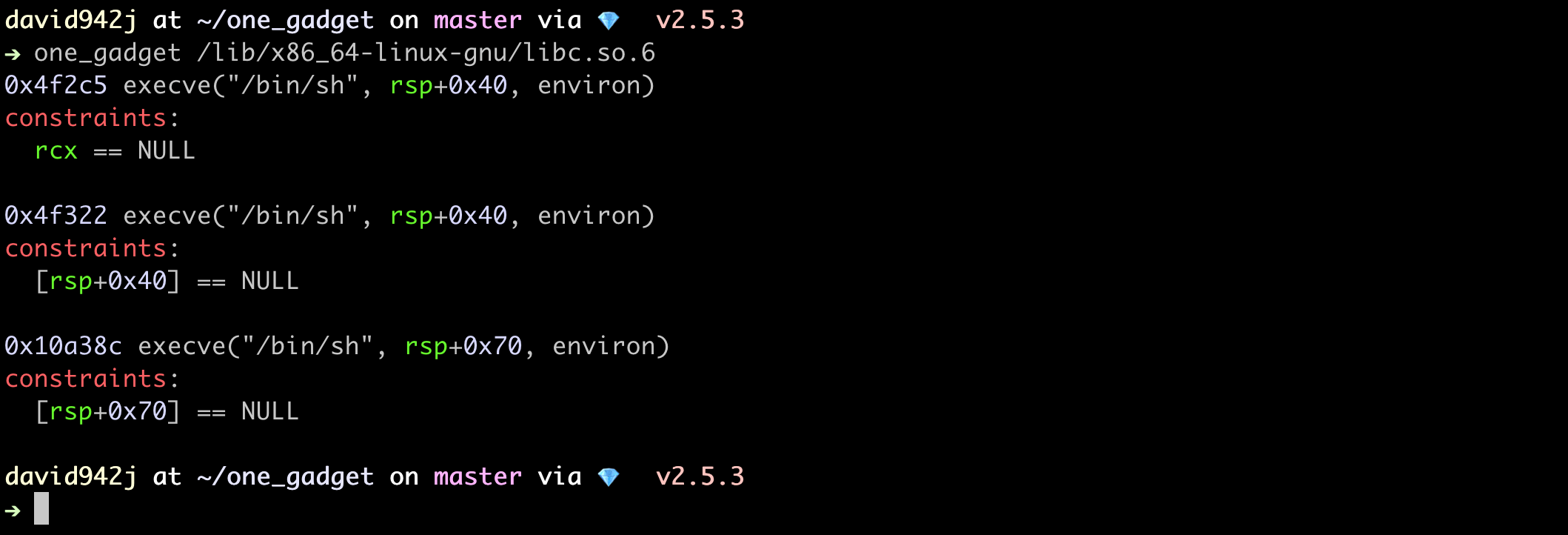
Before Start
This challenge took me 40 hours (including sleeping) to solve! One reason is I'm not familiar with race condition bugs. Main reason is because there're too many strategies (seems) can solve it. I have tried at least four kinds of exploitation and finally got the correct and stable one. I will show the final solution I got and mention why other solutions failed.
Another reason hard to solve this challenge is that race condition is difficult to debug because whenever a debugger presents, the race condition will always fail 😢
Basic Info
Challenge's attachment files can be found in my
github repo.
Source code, Makefile, and binary are given.
checksec of binary:
The Makefile is important, it reveals the compile options are:
$ clang-3.8 primary.c -Wall -Wextra -std=gnu11 -lpthread -O0 -o primary -ltcmalloc
It uses
tcmalloc as memory allocator which is a package in google-perftools.
This link has a nice explanation of it's malloc/free mechanism. I will briefly introduce it as well and explain how to exploit this kind of heap later.